Secure Your Business with BYOD Security Solutions
Protect your company’s data and networks with advanced BYOD security software. Safeguard personal devices used for work without compromising productivity.
Trusted by Renowned Customers & Partners
Overview
What Are BYOD Security Solutions?
BYOD (Bring Your Own Device) security refers to the policies, technologies, and practices that organizations implement to protect corporate data and systems when employees use their personal devices (e.g., smartphones, laptops, tablets) for work purposes. BYOD security solutions ensure safe access to corporate resources from personal devices. They ensure data protection without compromising user privacy.
The Problem
Why BYOD poses security risks for organizations?
Sensitive data theft
Phishing & ransomware attacks
Unsecured network access
Uncover risks and hidden costs
BYOD statistics by the numbers
91%
cybersecurity professionals reported an increase in cyber attacks due to remote work.
– Zipdo
30%
of organizations have zero visibility or control over employees’ mobile messaging.
- BitGlass
92%
remote workers use personal devices for work, 46% save work files on them.
– Lookout State of Remote Work Security survey
Solution Overview
Introducing Kitecyber’s BYOD Security Software
Kitecyber’s BYOD Security Solution keeps your business safe while enabling seamless work using any personal employee device.
Remote access VPN
Establish a secure, encrypted connection between your organization's network and remote employees or devices, effectively protecting all data transmitted over the internet.
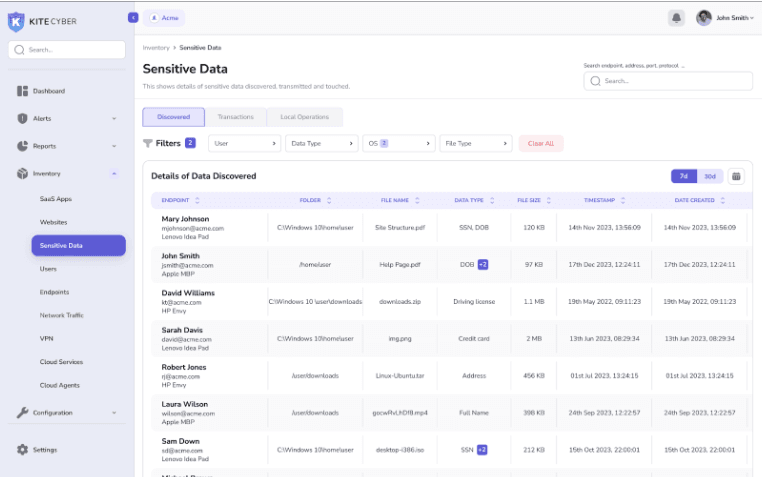
Data Loss Protection (DLP)
Secure your endpoints, internet, and SaaS apps used throughout the organization, seamlessly securing all the sensitive data for business critical purposes.
Secure Web Gateway
Block all internet-based ransomware threats before your employees click on them and share sensitive data.
Endpoint Management
Manage all your organization’s windows, linux, & apple endpoints seamlessly with a single unified console.
Stop online attacks at the source. Secure devices.
Detect threats at the moment of use, not during link sharing.
Our AI models activate directly on endpoints when a user clicks a link. Even if a link initially appears safe, attackers cannot delay poisoning to bypass BEC detection systems.
Omni Channel identity theft protection
Existing BEC tools have to scan all emails to look for any bad link. This is inefficient and can be easily bypassed using delayed link poisoning. They also don’t cover other channels from where a link can come like desktop apps, conferencing tools, instant messaging apps and social media.
DLP at rest and in motion
Sensitive data on employee devices poses significant security risks. Exposure of personal, health, or payment information can trigger serious compliance violations. Kitecyber scans Windows, macOS, and Linux devices for sensitive files. Take control by remotely encrypting or deleting data to stay secure and compliant.
Benefits
Why businesses choose Kitecyber to make BYOD devices secure?
Real-Time Threat Detection
Identify and neutralize threats such as insider theats, data exfiltration, and phishing attempts on BYOD devices.
Zero Trust Enforcement
Ensure all devices meet your organization's compliance security policies before granting access to corporate resources.
Advanced Endpoint Security
Use agentless or lightweight endpoint solution to secure unmanaged devices while preserving privacy.
Secure Data Access
Restrict access to sensitive resources with granular access controls and application sandboxing.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Case Studies
Customer Success Stories
Secure Your BYOD Environment Now!
Don’t let unsecured devices put your business at risk. Explore our BYOD security solutions today.
Frequently asked questions
FAQs on BYOD Security
BYOD (Bring Your Own Device) security refers to the policies, technologies, and practices that organizations implement to protect corporate data and systems when employees use their personal devices (e.g., smartphones, laptops, tablets) for work purposes. It ensures data protection without compromising user privacy.
- Personal devices are more vulnerable to cyber threats like malware and phishing.
- Corporate data accessed on personal devices can be exposed or leaked.
- Employees may not always follow security best practices on their personal devices.
- Implementing strong BYOD security ensures compliance, protects sensitive data, and mitigates potential risks.
- Device Diversity: Supporting various devices and operating systems.
- User Privacy: Balancing security measures without invading personal data.
- Policy Enforcement: Ensuring employees comply with security policies.
- Data Segmentation: Separating personal and corporate data effectively.
- Define a BYOD Policy: Set clear rules for device usage and security requirements. Use Multi-Factor
- Authentication (MFA): Add extra layers of security for access.
- Implement MDM or UEM Solutions: Manage and secure devices remotely.
- Enforce Data Encryption: Protect sensitive data at rest and in transit.
- Educate Employees: Train staff on recognizing threats and following security protocols.
- Enhanced Productivity: Employees can use devices they’re familiar with. Cost Savings: Reduces the need for company-provided devices.
- Improved Security: Protects corporate data on personal devices. Flexibility: Supports hybrid and remote work environments.
- Compliance: Ensures adherence to data protection regulations.
- Enforcing security policies like strong passwords and encryption. Allowing remote wiping or locking of lost/stolen devices.
- Monitoring devices to detect unauthorized access or malware.
- Controlling app installations to prevent unapproved or risky applications.
- MDM ensures that personal devices meet security standards without infringing on user privacy.