Enterprise Data Loss Prevention by Kitecyber
Trusted by Renowned Customers & Partners
Platform Overview
A secure and scalable DLP at the heart of your enterprise
Enterprises face enormous pressure. You must protect mountains of sensitive data. Stop data leaks and breaches before they happen. Follow strict security rules. Meet ever-changing compliance standards. And you have to do it all—without slowing down.
Kitecyber’s Enterprise Data Loss Prevention (DLP) Solution makes it possible.
Our solution gives you real-time sensitive data classification, smart access controls, and advanced encryption—so you can lock down critical data without locking down your business.
Protect customer, employee, and IP data at rest, in transit, and in use
Enforce granular access controls based on roles, devices, and locations
Detect sensitive data lineage on devices, internet & SaaS apps (Copy-paste activities, airdrop transfer, and USB)
Prevent sensitive data loss with remote lock & wipe—before damage is done
Enterprise Data Loss Prevention Solutions for Vertical Markets
Businesses in specialized industries, from healthcare and finance to manufacturing and retail, face unique challenges when safeguarding sensitive data. Regulatory demands, industry-specific risks, and complex operational workflows make it difficult to adopt generic, one-size-fits-all solutions.
Kitecyber Data Loss Prevention (DLP) is engineered to address the distinct needs of vertical markets, offering unmatched flexibility and precision. Unlike rigid platforms, Kitecyber enterprise DLP adapts to your industry’s compliance requirements, data workflows, and risk profiles. Customize policies, detection rules, and response protocols to align perfectly with your sector’s regulations—whether HIPAA, PCI DSS, GDPR, or niche mandates.
DLP for Financial Services
DLP for Healthcare
DLP for Manufacturing
DLP for Retail
DLP for Banking
DLP for Small Business
See. Secure. Simplify.
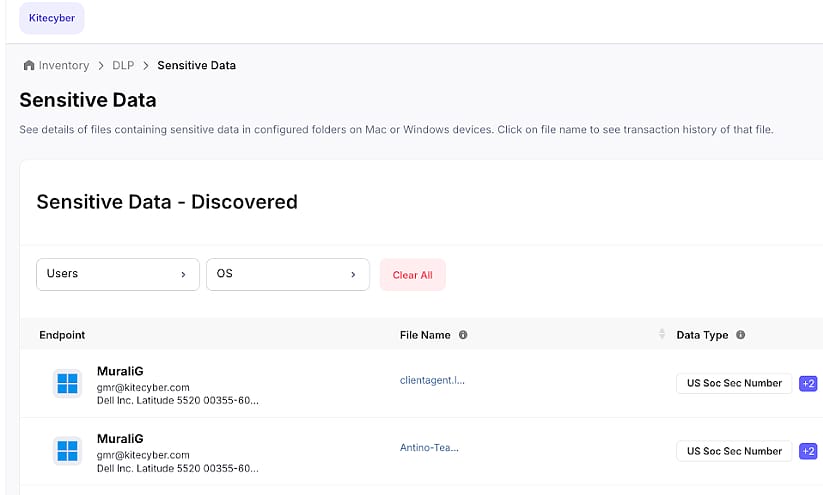
Find Sensitive Data Everywhere
Scan for sensitive data at rest, in motion, and in transit—across networks, devices, and SaaS apps. Enable secure use of GenAI tools without putting critical information at risk.
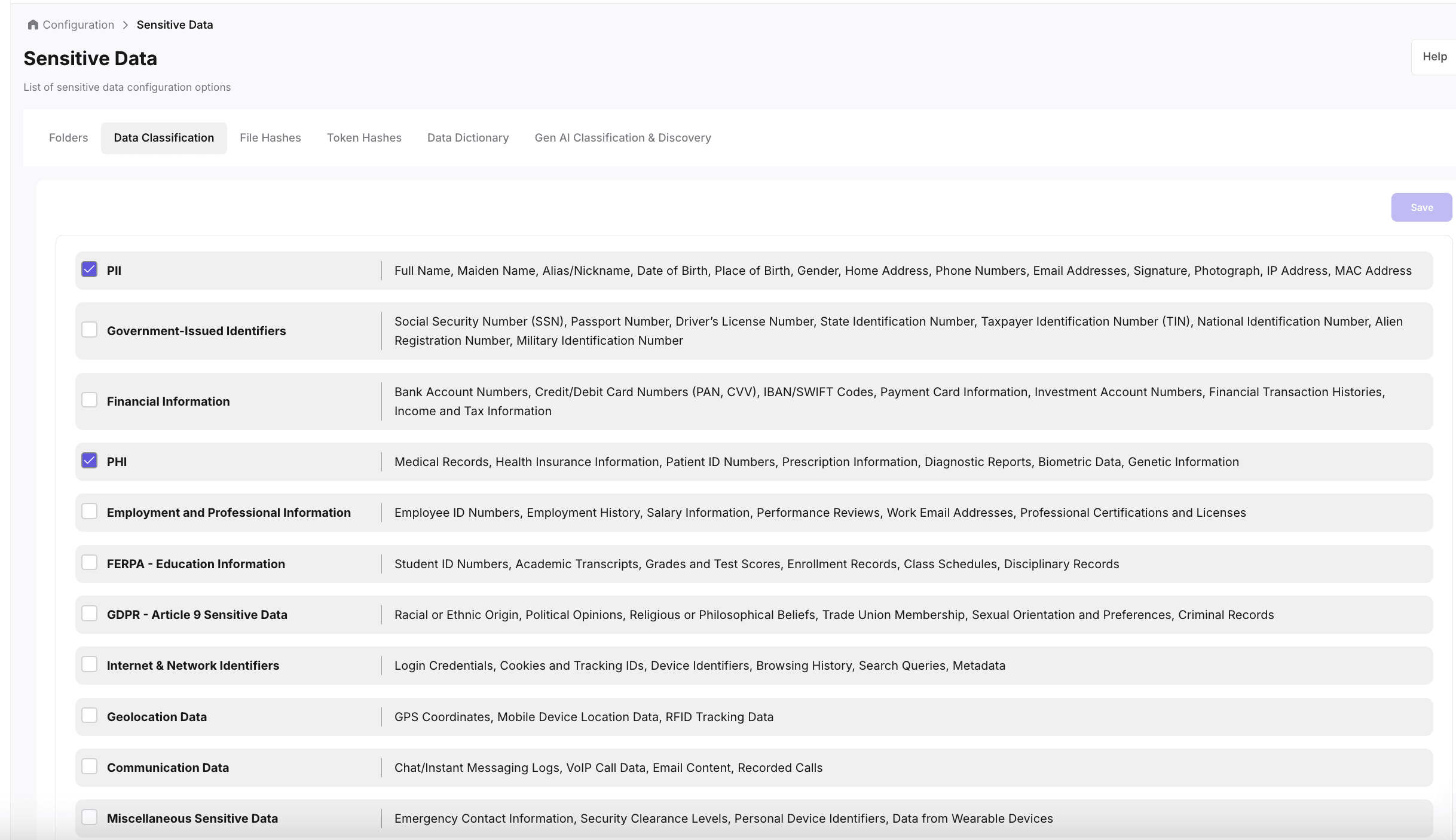
Classify Smarter with Device Trust
Kitecyber Device Shield provides complete visibility into device details, including model number, OS version, time zone, and security policies. Track haNo more guesswork. Classify any type of data, from files and screenshots to chat messages and images, using AI-powered Device Trust. Cut down false positives. Focus only on real threats. rd drive capacity, backup dates, and compliance status—ensuring your organization maintains full control and up-to-date information on every endpoint.
- 80+ Data Classifiers
- Constant data types update based on your feedback
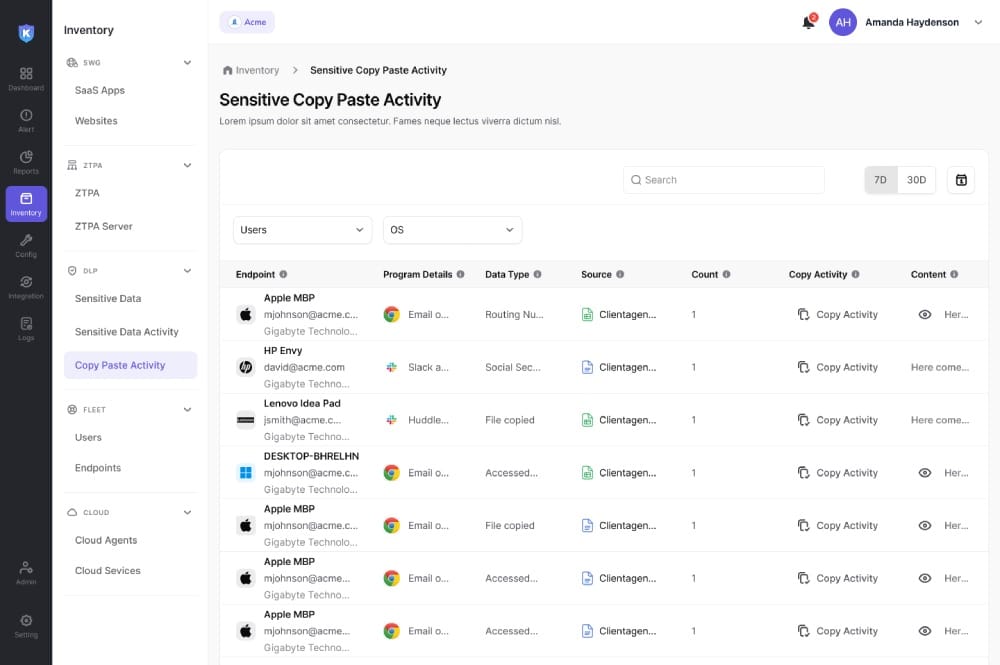
Track Insider Threats and Breaches
With deep visibility into user actions and context, you can spot suspicious behavior like sensitive data text copy-paste, airdrop transfer, USB transfer to prevent data exfiltration and keep your critical assets safe.
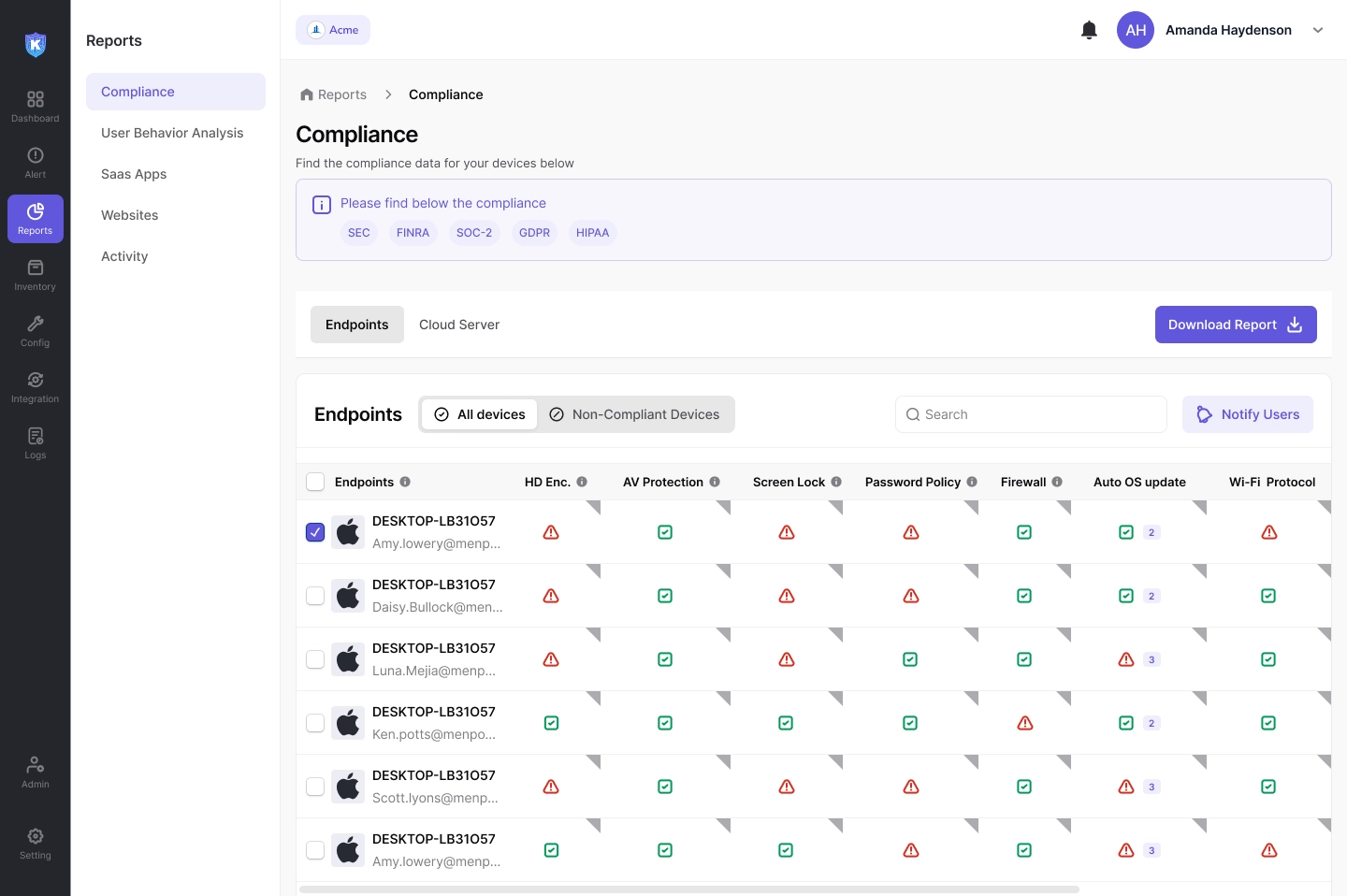
Enterprise Grade Security Without Compromise
By combining deep customization with enterprise-grade security, Kitecyber transforms DLP from a compliance obligation into a strategic asset. Industries with the most stringent demands trust us to reduce breach risks, streamline audits, and uphold customer trust—all while preserving the agility that drives their competitive edge.
Tailor every aspect of the solution:
Adaptable Policies
Define granular controls for data types critical to your industry, such as patient records, financial transactions, or intellectual property.
Vertical-Specific Workflows
Automate compliance checks and incident responses within existing processes, minimizing sensitive data theft.
Track sensitive data on devices
Tracks sensitive files—and even non-file data—from slipping out through untrusted web applications.
User Behavioral Analytics
Track sensitive data as it's copy-pasted, uploaded or downloaded within sanctioned corporate applications (AI or non-AI). Keep an eye on what matters most, ensuring your data stays protected.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Case Studies
Customer Success Stories
How it works
Frequently asked questions
There are three main types of DLP solutions:
- Network DLP: Monitors and controls data in motion across the network, such as emails and web traffic.
- Endpoint DLP: Protects data on endpoint devices (laptops, desktops, mobile devices) and can block unauthorized transfers to USB drives or other media.
- Cloud DLP: Secures data stored or processed in cloud applications and services, ensuring only authorized cloud usage158.
Pricing varies widely based on organization size, deployment type (cloud, on-premises, hybrid), and feature set. Typical costs range from $10 to $50 per user per month, with larger organizations potentially receiving volume discounts but facing higher initial setup costs.
- Classify and tag sensitive data at creation.
- Use both manual and automated data classification.
- Encrypt data at rest and in transit.
- Control access based on user identity, role, and context.
- Implement multi-factor authentication.
- Regularly review and update DLP policies.
- Train employees on data handling and security practices.
Consider the following when evaluating DLP vendors:
- Coverage for endpoints, networks, and cloud environments.
- Data discovery and classification capabilities.
- Ease of deployment and management.
- Integration with existing security tools.
- Support for regulatory compliance.
- Scalability and performance.
- Vendor reputation and support services