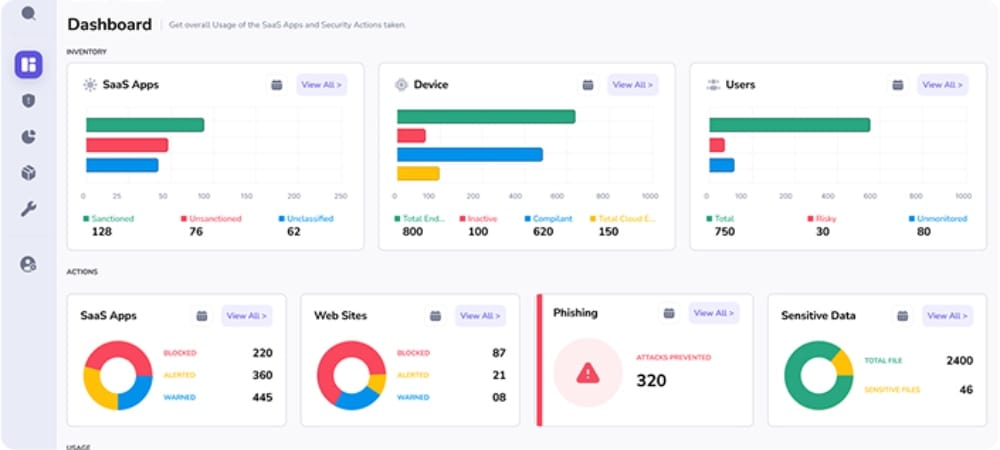
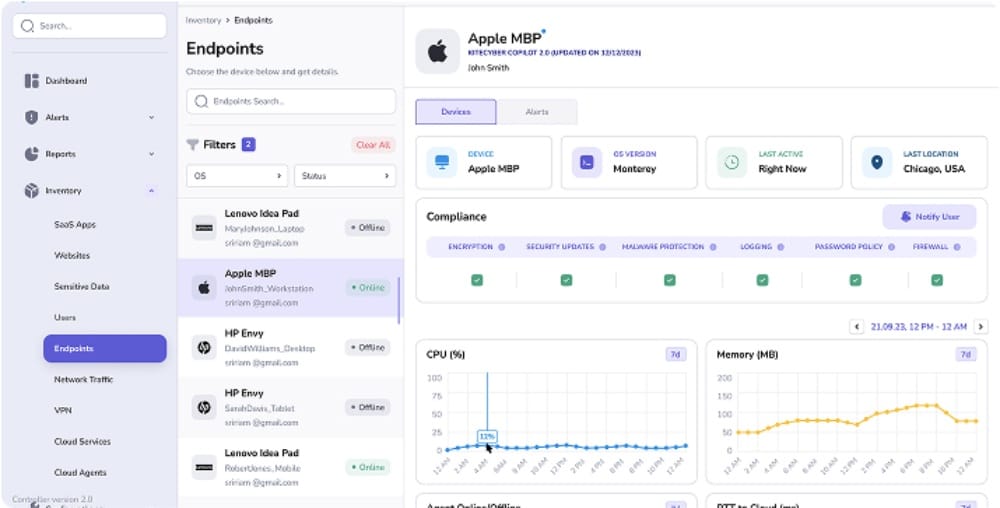
- 28 / 01 : Secure Slack Now: Protect Channels, Messages, and Sensitive URLs
- 22 / 08 : Elevating Collective Responsibility: How Kitecyber Empowers Your Cybersecurity Journey
- 03 / 07 : Navigating Off-Network security in the era of Modern Workforce
- 04 / 06 : Choosing the Ultimate Private Access Solution: VPN, ZTNA, or Beyond
- 27 / 05 : Shadow SaaS: What Every CISO Needs To Know
- 28 / 01 : Secure Slack Now: Protect Channels, Messages, and Sensitive URLs
- 22 / 08 : Elevating Collective Responsibility: How Kitecyber Empowers Your Cybersecurity Journey
- 03 / 07 : Navigating Off-Network security in the era of Modern Workforce
- 04 / 06 : Choosing the Ultimate Private Access Solution: VPN, ZTNA, or Beyond
- 27 / 05 : Shadow SaaS: What Every CISO Needs To Know
Product
Solutions
Company
Contact Us
- 691 S Milpitas Blvd, Ste 217, Milpitas, CA 95035

- We are SOC 2 Type II compliant