Data Security Solution
Discover, Visualize and Control all your sensitive data
Trusted by Renowned Customers & Partners
Overview
The limitations of traditional in-network DLP solutions
Data leaks aren’t always external. Your sensitive data faces risks from careless actions like upload, copy-paste, and airdrop usage, malicious intent, and compromised accounts. In-network DLP solutions like SASE often miss to track these malicious actors. You can’t rely on outdated tools. It’s time for a smarter solution.
The Problem
The Challenges with In-network Data Security Solutions
Leave most network traffic including NON-TCP uninspected, creating data blindspots;
Fail to analyze privacy-sensitive data on devices
Doesn’t support all filetypes and sizes, including no offline capabilities.
| Agentic AI Apps | Insider Threats |
|---|---|
| Operate autonomously, bypassing traditional platforms and exposing sensitive data. | Password-protected or encrypted files aren’t supported by network DLP solutions, leaving data movement due to insider misuse undetected. |
| Exploitative prompts can override role-based access controls. | Exploitable limitations in file types and sizes. |
Why does Data Security matter?
78%
organizations experienced a data breach even with DLP in place.
50%
of workers who changed jobs within the last two years admitted to taking data when they left
62%
of organizations do not have a mature data loss prevention (DLP) program in place
Product Overview
Introducing Data Shield: Kitecyber’s Data Security Solution
Kitecyber’s Data Shield unifies endpoint and in-network DLP for complete data security. It leverages endpoint and network signals to defend against threats like insider misuse and Agentic AI apps. From day one, it tracks sensitive data movement across devices, email, SaaS apps, and networks. By filtering user-behavior and activity, Kitecyber lets you focus on securing sensitive data from insider theft and exposure.
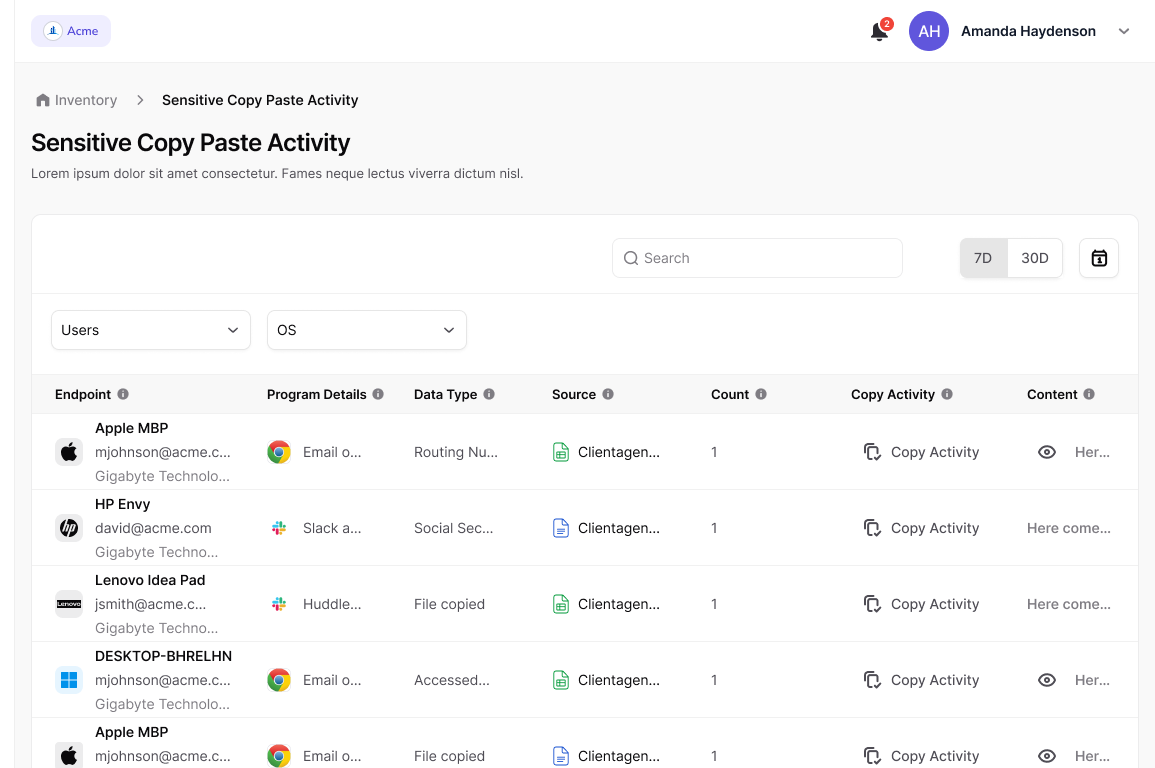
Identify and protect sensitive data across all devices
Stop data exfiltration before it happens
Secure sensitive information—such as PII and ePHI—by detecting and stopping copy-paste activities, email attachments, and insider threats. Stay ahead of potential breaches with proactive monitoring and automated threat mitigation.
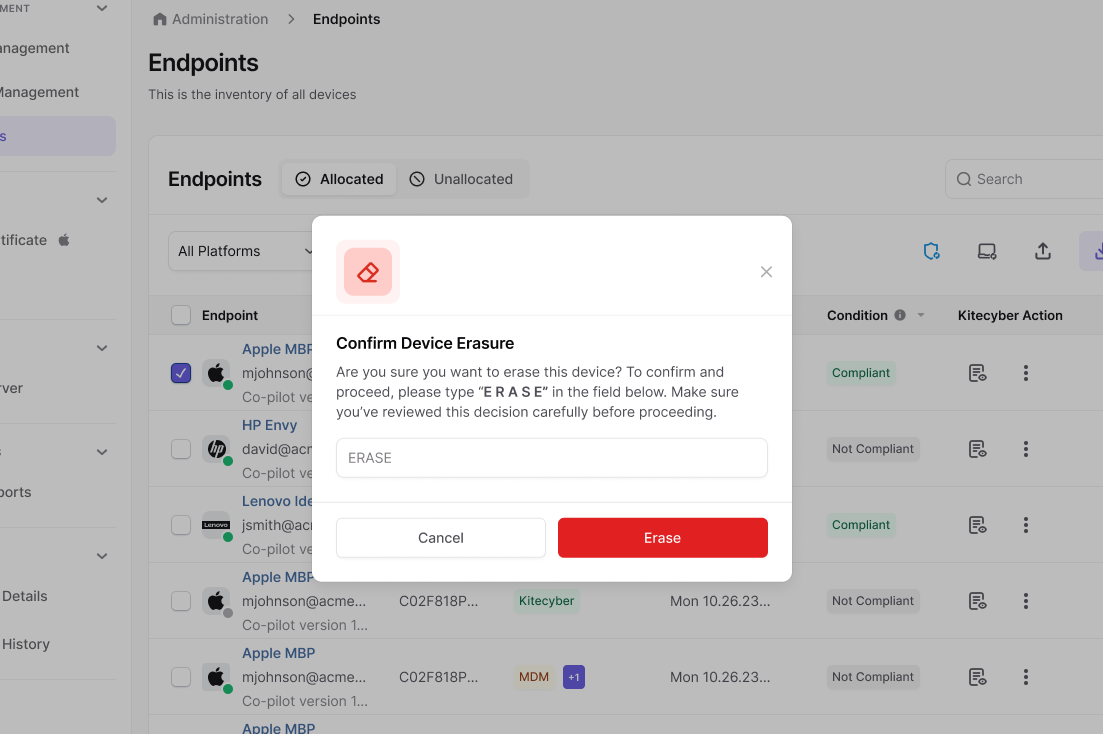
Instantly erase data to prevent unauthorized access
Secure lost or stolen devices with a single action
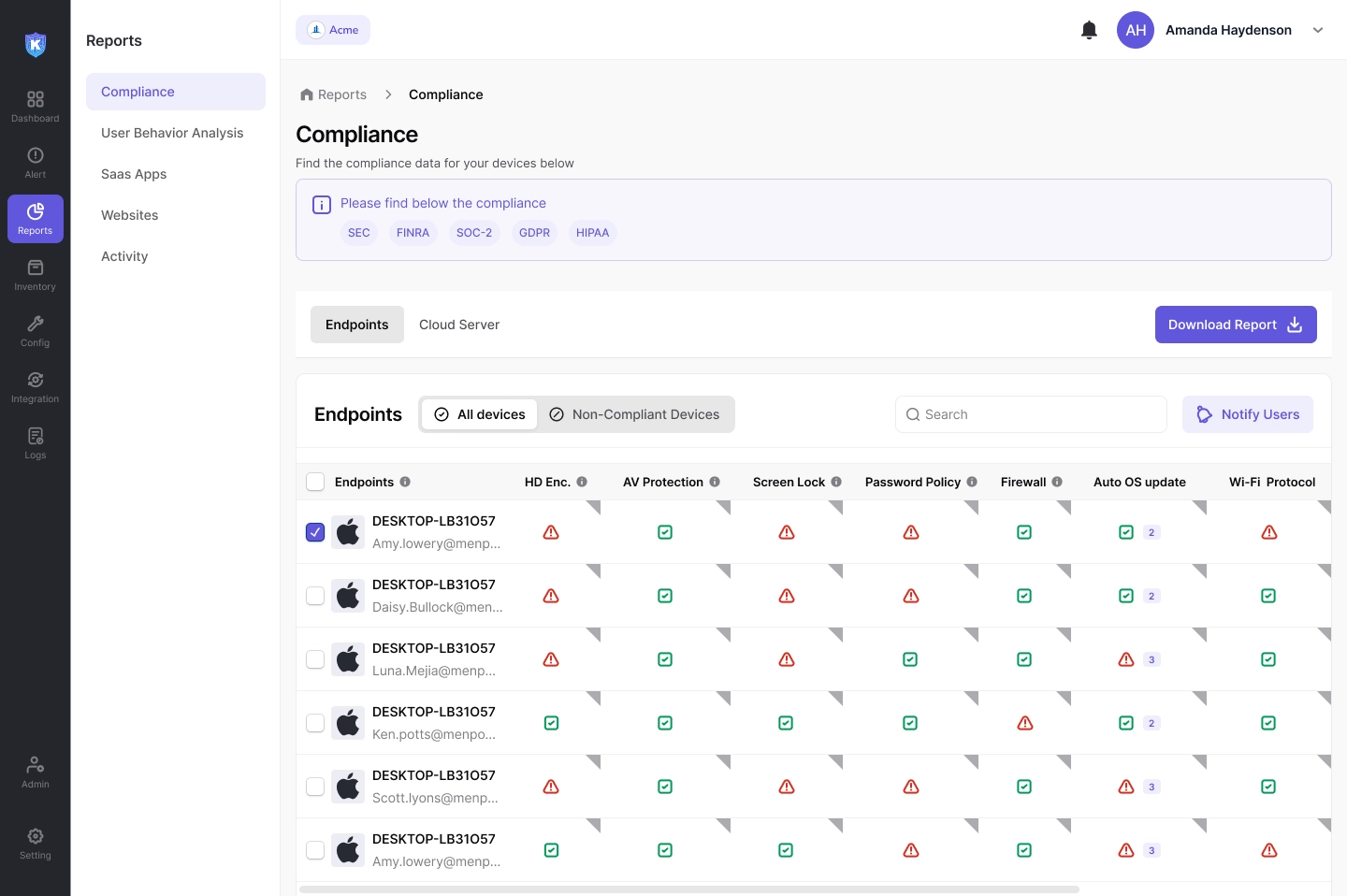
Enforce regulatory compliance and prevent data theft
Why choose Kitecyber?
| Data Discovery & Protection | Kitecyber Data Shield | In-Network DLP (SASE) |
|---|---|---|
Data discovery & Security | HighWorks without exceptions | WeakDoes not work for End-to-End encrypted apps or data that’s password protected or encrypted |
Data Lineage | ComprehensiveAt rest on user device, user activity and network activity | PartialLimited to network visible activity for non encrypted data |
Privacy | YesSelf hosted or SaaS | No3rd Party Cloud |
Compliance | Covered | Gaps |
Performance & Scaling | High | Poor scaling & performanceMultiple levels of traffic redirections with decryption and re-encryption |
Onboarding | SimpleZero Touch Provisioning in minutes | ComplexRequires skilled professional services with weeks to deploy |
Cost | CheaperLeverage edge computer | ExpensiveCloud based solution |
The Kitecyber Advantage
- Before Kitecyber Data Shield
- In-network DLPs only detect what they’re programmed for, leaving real risks like agentic AI apps and insider threats unnoticed.
- IT waits for about 2 months to deploy hard-to-configure DNS rules, which frustrates employees
- In-network DLPs leave scanning all file types and ignore files of bigger size.
- After Kitecyber Data Shield
- Kitecyber Data Shield runs on your endpoint, adapts to users behaviour, and detects all shadow AI, supply chain apps, and insider actions.
- IT starts tracking sensitive data movement in a few days after copilot deployment.
- Kitecyber Data Shield scan files of all types and sizes .
Use-case
Ensure data security and compliance without slowing teams
Regulatory Compliance
Ensure adherence to industry regulations like GDPR, HIPAA, and PCI DSS by safeguarding sensitive data across endpoints and SaaS platforms.
Protection of Confidential Information
Defend your intellectual property and business secrets from breaches caused by insider threats or external attacks.
Prevention of Data Exfiltration
Stop unauthorized data transfers by monitoring and controlling sensitive information flows across your network
Maximizing Data Visibility and Compliance for a Growing Financial Firm
A rapidly expanding financial firm operating in a highly regulated environment, managing large volumes of sensitive customer and financial data.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Case Studies
Customer Success Stories
How it works
Frequently asked questions
Data Security software is a set of tools and processes used to protect sensitive data within an organization by preventing unauthorized access, sharing, or transfer of information. Data security software monitors data in use, in motion, and at rest, enforcing policies to safeguard against data leaks and loss, whether from accidental errors or malicious activities. It’s particularly useful in protecting sensitive information such as financial data, intellectual property, and personally identifiable information (PII).
Data Security is essential for organizations because it protects against the loss or misuse of sensitive data, which can result in severe financial, legal, and reputational damage. With regulatory requirements such as GDPR, HIPAA, and CCPA, organizations are legally obligated to protect certain types of information. DLP software helps meet compliance requirements, avoid data breaches, and maintain customer trust by ensuring sensitive data remains secure and used according to policy.
Key features of Data Security software include:
Data Discovery and Classification: Identifying sensitive data and categorizing it by type and importance.
Content Monitoring and Filtering: Tracking data movement and enforcing security policies based on data type or context.
Policy Enforcement: Enforcing customizable rules to allow or block certain actions, such as data sharing or uploading.
Encryption and Access Control: Encrypting sensitive data and restricting access to authorized users.
Incident Response and Reporting: Providing alerts, logs, and reports to help identify potential threats and respond to incidents quickly.
Kitecyber’s data security software protects data in three primary states:
Data in Use: Kitecyber Data Shield monitors data actively being used on devices, such as files being edited or transferred, and ensures sensitive information is handled appropriately.
Data in Motion: It inspects data as it travels over the network, blocking unauthorized sharing or transmission outside of the secure environment.
Data at Rest: Kitecyber Data Shield secures stored data within databases, servers, and other storage systems, detecting potential risks and enforcing policies to protect sensitive information from unauthorized access or accidental exposure.
Common challenges with data security implementation include:
Complexity of Deployment: Configuring DLP software to work across various devices and environments can be complex, especially in large organizations.
User Privacy Concerns: Monitoring data activities can raise privacy issues, making it essential to balance security with user privacy.
High False Positives: DLP tools may trigger false positives, flagging legitimate activities as threats, which can overwhelm security teams.
Scalability: As organizations grow, scaling DLP solutions to accommodate more data sources and endpoints can be challenging.
Maintenance and Policy Updates: DLP policies require regular updates to adapt to new threats, regulatory requirements, and organizational changes.