Picture this: A single click on a phishing email just cost your company millions. Customer data leaked, trust shattered, and regulators knocking. Unfortunately, this nightmare is all too common. As cyberattacks grow more sophisticated, ransomware alone surged by 150% last year, the stakes have never been higher.
As per various sources, a single data breach can:
But here’s the good news: You don’t need a cybersecurity PhD to protect your data. In this guide, we’ll break down data security into simple, actionable steps. By the end of this guide, you’ll have a clear roadmap on how to secure sensitive data and sleep easier knowing your business isn’t the next data leak headline.
Let’s get started.
What is Data Security?
Before we explore how to protect sensitive information, it is essential to first grasp the fundamentals of what data security is. In its simplest form, data security refers to the practices and technologies implemented to safeguard digital information from unauthorized access, corruption, or theft throughout its lifecycle.
In today’s interconnected world, data plays a critical role in nearly every aspect of our lives. From personal details like banking information and medical records to confidential business plans and intellectual property, the value of data cannot be overstated. However, this reliance on data also makes it a prime target for malicious actors. According to cybersecurity experts, the frequency and sophistication of data breaches are on the rise, posing significant risks to individuals and organizations alike.
With millions of cyberattacks occurring annually, many of which aim to exploit vulnerabilities and steal sensitive information, taking proactive steps to secure data has never been more important. Whether it is protecting customer information, securing financial transactions, or ensuring compliance with regulatory standards, robust data security measures are vital.
Secure Your Business Critical Data with Kitecyber Data Shield. Track Data Lineage, User Behavior Analysis (UBA), and Secure Data Leak.
Why Do You Need Protected Data?
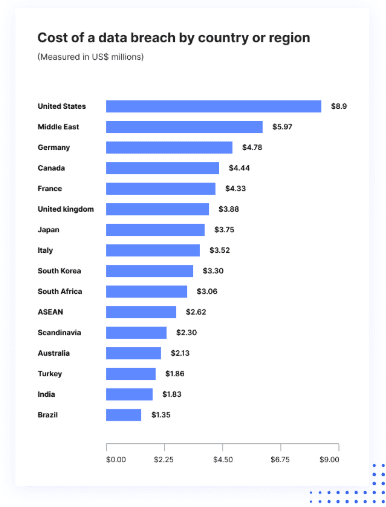
Sensitive data leaks don’t just disrupt businesses—they can destroy them. A single breach can jeopardize financial stability, erase years of hard work, and severely damage a company’s reputation. For small and medium-sized businesses operating across borders, the cost of a data breach varies, but it often reaches millions of dollars.
When your data is exposed, stolen, or held for ransom, the impact goes beyond lost revenue. A compromised business data can be defaced, misleading customers and eroding trust. Worse, hackers can use it as a launchpad for further attacks, putting your partners and users at risk.
Data protection isn’t optional—it’s essential.
What Types of Sensitive Data Should You Secure?
Sensitive information is any data that, if exposed, could lead to chaos: financial ruin, reputational damage, or illegal access. Examples of sensitive data include: social security numbers, bank accounts, business patents, medical histories, or trade secrets.
These types of data are often regulated by laws and must be handled with care to ensure privacy and security.
Organizations should ensure complete protection of following categories of sensitive data:
1. Personally Identifiable Information (PII)
PII includes any information that can directly or indirectly identify an individual. Examples include:
Regulations like GDPR, CCPA, and HIPAA govern how PII is collected, processed, and stored.
2. Personal Information (PI)
PI is a broader category that encompasses any data capable of identifying an individual, either directly or indirectly. It overlaps with PII but may vary based on jurisdictional definitions. Examples include:
Protecting PI is critical to prevent identity theft, fraud, and privacy violations.
3. Sensitive Personal Information (SPI)
SPI refers to highly sensitive data that could cause harm if disclosed. It includes:
SPI is specifically addressed under regulations like the California Privacy Rights Act (CPRA).
4. Nonpublic Personal Information (NPI)
NPI is sensitive financial information protected under the Gramm-Leach-Bliley Act (GLBA). It includes:
NPI excludes publicly available information and applies primarily to financial institutions.
5. Material Nonpublic Information (MNPI)
MNPI refers to confidential corporate data that could influence stock prices if disclosed. Examples include:
MNPI is regulated under securities laws to prevent insider trading.
6. Private Information (New York SHIELD Act)
Under New York’s SHIELD Act, private information includes combinations of personal data that could lead to identity theft. Examples are:
This definition expands upon traditional “personal information” by focusing on data combinations.
7. Protected Health Information (PHI / ePHI)
PHI refers to medical information that identifies an individual and is regulated under HIPAA. It includes:
When stored digitally, PHI is referred to as electronically Protected Health Information (ePHI).
8. Business-Specific Sensitive Data
Beyond regulated categories, organizations may handle proprietary or confidential business data, such as:
These datasets often overlap with other sensitive data types (e.g., PI, PII, SPI) but require custom classification and handling based on business needs.
Take the First Step Toward Unbreakable Data Security
Discover and classify sensitive business data across devices & SaaS apps with Kitecyber Data Shield.
What are the common threats to data security?
Data security faces numerous threats that can compromise sensitive information, disrupt operations, and cause financial or reputational damage. Below are some of the most prevalent threats and their implications:
Malware refers to malicious software designed to infiltrate, damage, or gain unauthorized access to computer systems. It includes ransomware, spyware, viruses, worms, and more. These programs often spread through infected files, email attachments, unsecured websites, or malicious downloads.
Phishing attacks involve cybercriminals posing as trustworthy entities to trick individuals into revealing sensitive information, such as passwords, credit card details, or personal data. These attacks often occur through deceptive emails, fake websites, or urgent messages designed to manipulate users.
Insider threats arise when individuals within an organization misuse their access privileges, either intentionally or unintentionally, leading to data breaches or leaks. These threats can come from negligent employees, malicious insiders, or third-party vendors with access to sensitive systems.
Physical theft involves the unauthorized removal or loss of devices such as laptops, smartphones, or storage media containing sensitive information. This type of threat can lead to data exposure if stolen devices are not properly secured.
Human error encompasses unintentional mistakes, misconfigurations, or lapses in judgment that can expose data or create vulnerabilities. Examples include falling victim to phishing scams, failing to apply software updates, or mishandling sensitive information.
DoS and DDoS attacks aim to overwhelm servers, networks, or applications with excessive traffic, rendering them inaccessible to legitimate users. These attacks disrupt services and cause downtime by exhausting system resources.
How to Secure Sensitive Data Using CIA Triad
Take charge of your data security. Don’t wait for attackers to exploit vulnerabilities—stay ahead of the data security threats, whether internal or external.
From applying regular security updates to monitoring for suspicious activity, small proactive steps can make a big difference.
The CIA Triad: Confidentiality, Integrity, and Trustworthiness
Cybersecurity is built on three key principles: Confidentiality, Integrity, and Availability, commonly known as the CIA triad. This model helps organizations protect their sensitive data and systems from cyber threats. Let’s break down each component and explore how they work together.
Confidentiality: Protecting Sensitive Information
Confidentiality ensures that only authorized people or systems can access sensitive data. If this principle is broken, personal information, trade secrets, or financial records could fall into the wrong hands.
1) Access Control
Implement role-based access control to limit data exposure by ensuring that only authorized personnel can access specific systems or data. Strong authentication methods, such as passwords, should be used for basic security, while multi-factor authentication (MFA) and biometric authentication provide additional layers of protection. Regularly reviewing and updating user roles and permissions ensures that access remains appropriate and necessary. Unused accounts should be disabled promptly, and unnecessary privileges revoked to minimize the risk of unauthorized access. By combining these measures, organizations can maintain a robust access control framework that adapts to evolving security needs.
2) Encryption
Encrypting stored data, also known as data at rest, is essential to safeguard sensitive information from breaches. Protocols like AES ensure that data remains secure on disks, while encryption during transmission, or data in transit, prevents interception over networks. SSL/TLS protocols are commonly used to secure communications over the internet, and encryption keys must be managed securely, with regular rotation to maintain their effectiveness. Avoid storing sensitive data in plain text at any stage, and regularly test encryption mechanisms to ensure they remain robust against emerging threats.
3) Email Security and Anti-Phishing Measures
Implementing advanced email filtering is a critical step in blocking phishing attempts before they reach employees. Domain authentication protocols like DMARC, DKIM, and SPF help verify the legitimacy of emails, reducing the risk of spoofing attacks. Real-time threat detection systems can identify and neutralize malicious emails, ensuring that only safe communications reach users. By combining these measures, organizations can significantly reduce the likelihood of successful phishing attacks. Regular updates to filtering rules and threat intelligence databases ensure that defenses remain effective against evolving tactics. Educating employees on recognizing phishing emails further strengthens this layer of security. A proactive approach to email security minimizes risks and protects sensitive business data from compromise.
4) Endpoint Security
Endpoint security protects multi-OS devices like
windows,
linux, and
mac OS from cyber threats that could compromise sensitive data. Installing antivirus software and keeping it updated is a fundamental step, while enabling firewalls blocks unauthorized access attempts. Device encryption secures data stored locally, and strict password policies, combined with regular updates, enhance endpoint security. Promptly applying patches and updates fixes known vulnerabilities, and device management solutions provide centralized control for managing endpoints. By securing endpoints, organizations reduce the risk of breaches originating from compromised devices.
5) Insider Threat Monitoring
Deploying user behavior analytics (UBA) helps detect suspicious activities, such as unusual data access patterns or large data transfers, which may indicate insider threats. UBA systems analyze normal user behavior and flag anomalies that could signify malicious intent. Monitoring privileged user activities is particularly important, as they have access to critical systems and
Auditing and monitoring are essential for tracking who accesses sensitive data and detecting suspicious activity. Logging tools record system and user activities, enabling organizations to analyze logs regularly for unusual patterns or anomalies. Setting up alerts for suspicious activities, such as unauthorized login attempts, allows for quick responses to potential threats. Conducting periodic audits ensures compliance with security policies and identifies areas for improvement. Automated tools streamline monitoring and reporting processes, making it easier to address identified vulnerabilities or incidents promptly and mitigate risks effectively.
Integrity: Ensuring Data Accuracy and Preventing Tampering
Data integrity ensures that business information remains unaltered and trustworthy, protecting it from manipulation by insider threats or phishing-induced malware infections.
How to Secure Sensitive Information and Prevent Data Integrity
1) Digital Signatures and Hashing
Using digital signatures and cryptographic hash functions ensures the authenticity and integrity of sensitive documents and emails. Digital signatures verify the identity of the sender and confirm that the content has not been altered during transmission. Hash functions generate unique identifiers for files, enabling organizations to detect unauthorized modifications. These technologies are essential for preventing tampering and maintaining data accuracy. Regularly updating cryptographic data. Combining UBA with real-time alerts enables quick responses to potential threats, minimizing damage. Regular reviews of monitoring logs and incident reports help refine detection algorithms. By proactively identifying and mitigating insider threats, organizations protect sensitive business data from internal risks.
2) Audit Logs and Version Control
Maintaining immutable audit logs and version control systems ensures accountability and tracks changes to sensitive business data. Audit logs record who accessed or modified data and when, providing a transparent trail for investigations. Version control allows organizations to revert to previous states in case of unauthorized changes or errors. Automating log management reduces the risk of tampering and ensures compliance with regulatory requirements. Regular reviews of audit logs help identify patterns of misuse or suspicious activities. These measures are critical for preserving data integrity and preventing unauthorized modifications.
3) Endpoint Detection and Response (EDR)
Deploying Endpoint Detection and Response (EDR) solutions helps detect malware infections from phishing attacks that attempt to modify or corrupt data. EDR systems provide real-time monitoring and analysis of endpoint activities, identifying suspicious behaviors and mitigating threats quickly. Advanced threat detection capabilities enable organizations to respond to incidents before significant damage occurs. Integrating EDR with other security tools creates a comprehensive defense strategy. Regular updates and patch management ensure endpoints remain protected against emerging threats. This proactive approach minimizes the risk of data tampering and ensures business continuity.
4) Data Loss Prevention (DLP)
Data Loss Prevention (DLP) tools help monitor and control outgoing data to detect unauthorized transfers or potential leaks. These tools enforce policies on how sensitive data is handled, blocking or flagging suspicious activities such as large file uploads. Classifying data based on sensitivity allows organizations to prioritize protection efforts effectively. Employee training plays a crucial role in recognizing and avoiding risky data-sharing behaviors, and
endpoint DLP rules should be updated regularly to adapt to new threats and workflows. Periodic reviews ensure that DLP measures remain effective and aligned with organizational goals.
5) Regular Integrity Checks
Automating integrity monitoring ensures that unauthorized changes in databases, applications, or critical files are detected promptly. Integrity checks compare current file states with baseline hashes, identifying discrepancies that may indicate tampering. Real-time alerts notify administrators of suspicious activities, enabling swift responses to potential threats. Regularly scheduling integrity scans ensures continuous protection against unauthorized modifications. Combining integrity checks with other security measures creates a robust defense strategy. This proactive approach preserves the accuracy and reliability of business data.
6) Strict Vendor and Third-Party Security Policies
Ensuring that partners and suppliers handling sensitive business data follow stringent security practices is essential for maintaining trust and compliance. Organizations should conduct thorough assessments of third-party security controls before granting access to critical systems. Contracts should include clauses mandating adherence to specific security standards and regular audits. Monitoring vendor activities and enforcing strict data-handling policies reduces the risk of breaches. Collaborating with trusted partners ensures that sensitive business data remains protected throughout the supply chain.
Availability: Ensuring Access to Critical Business Data
How to Secure Sensitive Information and Prevent Data Integrity
Availability guarantees that sensitive business data remains accessible to authorized users while preventing disruptions from phishing-related attacks or malicious insiders.
How to Secure Sensitive Information and Ensure 100% Availability
1) Disaster Recovery and Backup Plans
Implementing automated, secure backups is vital for restoring data quickly in case of deletion or ransomware attacks resulting from phishing schemes. Regular backups ensure that critical business data remains accessible even during disruptions. Storing backups in secure, offsite locations protects against physical disasters and cyberattacks. Testing recovery plans periodically ensures their effectiveness and identifies areas for improvement. By prioritizing disaster recovery, organizations minimize downtime and maintain business continuity in the face of unexpected incidents.
2) Endpoint and Insider Threat Detection Systems
Deploying real-time monitoring systems prevents unauthorized deletion or encryption of critical data by insiders or malware. These systems track endpoint activities and flag suspicious behaviors, enabling quick responses to potential threats. Combining endpoint detection with insider threat monitoring provides comprehensive visibility into data access patterns. Regular updates and patch management ensure endpoints remain protected against emerging risks. By addressing both external and internal threats, organizations safeguard the availability of sensitive business data.
3) Network Segmentation and Zero Trust Security Model
Restricting access to critical business systems through network segmentation and the Zero Trust security model ensures that unauthorized users cannot affect availability. Zero Trust principles require continuous verification of user identities and device health before granting access. Segmenting networks limits the spread of malware and isolates sensitive systems from less secure areas. Regularly reviewing access policies ensures they remain aligned with organizational needs. This strategy minimizes the attack surface and enhances the resilience of critical business operations.
4) Redundancy and Failover Mechanisms
Maintaining redundant systems and load balancers ensures seamless business operations even during cyberattacks or system failures. Redundancy eliminates single points of failure, while failover mechanisms automatically redirect traffic to backup systems. Regularly testing these systems ensures they function as intended during emergencies. By investing in redundancy and failover, organizations guarantee uninterrupted access to critical business data. This approach supports operational resilience and customer satisfaction.
5) Regular Security Audits and Penetration Testing
Simulating phishing attacks and insider threat scenarios through regular security audits and penetration testing identifies vulnerabilities before they are exploited. These exercises evaluate the effectiveness of existing security measures and highlight areas for improvement. Comprehensive reports guide decision-making and resource allocation for strengthening defenses. Conducting audits periodically ensures ongoing compliance with industry standards and regulations. By adopting a proactive stance, organizations stay ahead of emerging threats and protect sensitive business data.
Have a data security plan before disaster strikes
No matter how secure your systems are, cyber threats like phishing attacks and insider breaches can still happen. Be ready with a solid recovery plan. Regularly test it with your team to ensure everyone knows their role when a security incident occurs.
Data security isn’t a one-time task—it’s an ongoing process. New threats emerge daily. If a breach happens, act fast to recover your data, restore operations, and analyze what went wrong. Then, strengthen your defenses to prevent it from happening again.
Protect your business by staying proactive. Secure your sensitive data, monitor risks, and always have a plan in place. Try Kitecyber Data Shield to secure sensitive data, monitor insider threats using user-behavioral analytics, and lock devices in case of any theft.
Protect What Matters Most – Your Sensitive Data
Unlock the power of Kitecyber Data Shield, the ultimate solution for discovering and classifying sensitive business data across devices and SaaS apps.