Device management & security
Unified Endpoint Management Solution
Manage all devices, apps & data—across platforms and operating systems—from one centralized console.
Kitecyber’s Unified Endpoint Management (UEM) Solution makes it easy to manage devices while keeping security streamline.
Trusted by Renowned Customers & Partners
Overview
Manage endpoints while keeping sensitive data secure
Today, most employees access sensitive business data outside office premises due to the advent of remote work culture. They bypass firewalls and traditional security systems, which makes protecting sensitive data more difficult. You need robust yet simple UEM tools, so you can:
Enforce powerful security policies everywhere
Respond to data theft incidents more quickly and efficiently
Track user behavior like copy-paste, USB transfer, etc more effectively.
The Problem
Traditional MDM approach to managing endpoints is broken
Mobile Device Management (MDM) tools help with basic device endpoints control, but they fail to provide full security with gaps like:
Limited Data Protection
MDM secures devices, but it doesn’t stop data leaks across SaaS apps, emails, internet, USB and Airdrop transfer.
Weak Threat Prevention
It lacks real-time protection against phishing, ransomwares, and insider threats.
No Visibility Into User Behavior
MDM can track devices but doesn’t monitor risky actions or unauthorized data access.
Poor Coverage for BYOD/ Hybrid Work
Employees use personal laptops, tablets, and mobile phones, which MDM can’t fully control.
Compliance Gaps
Meeting SOC 2, ISO 27001, and GDPR requires data security beyond device management.
Multi-OS endpoints are easy target for data leaks
70%
businesses using Mac devices report experiencing cyberattacks.
– market.us scoop
68%
firms had suffered one or more endpoint assaults that successfully compromised data and/or IT infrastructure.
– market.us scoop
75%
malware targeting Linux endpoints in 2023 exploited outdated software.
– Linux Threat Report, 2023
Product Overview
Introducing Kitecyber’s
Unified Endpoint Management (UEM) Solution
Kitecyber’s UEM solution brings both endpoint management & security under one roof. It lets you manage all devices and track events and system health metrics like CPU and memory usage.
Unified control for every endpoint, everywhere
Manage all endpoints effortlessly from a single, intuitive dashboard. Discover, configure, and secure every device with Kitecyber’s Unified Endpoint Management solution.With just a few clicks, enforce policies, manage privileges, and proactively resolve endpoint issues—ensuring seamless security and an optimized user experience.
Full transparency and control
over every device
Kitecyber Device Shield provides complete visibility into device details, including model number, OS version, time zone, and security policies. Track hard drive capacity, backup dates, and compliance status—ensuring your organization maintains full control and up-to-date information on every endpoint.
Seamless endpoint assignment and lifecycle management
Efficiently assign, unassign, or delete business endpoints with Kitecyber Device Shield. Track the location, owner, and configuration of each device before and after deployment. When a device becomes outdated or non-functional, easily remove it from the system—ensuring efficient IT asset management.
Instant data protection with remote wipe
Safeguard sensitive business data by enabling instant data wiping on compromised devices. In case of theft or loss, this feature ensures confidential information remains secure and inaccessible, preventing data leaks and unauthorized access.
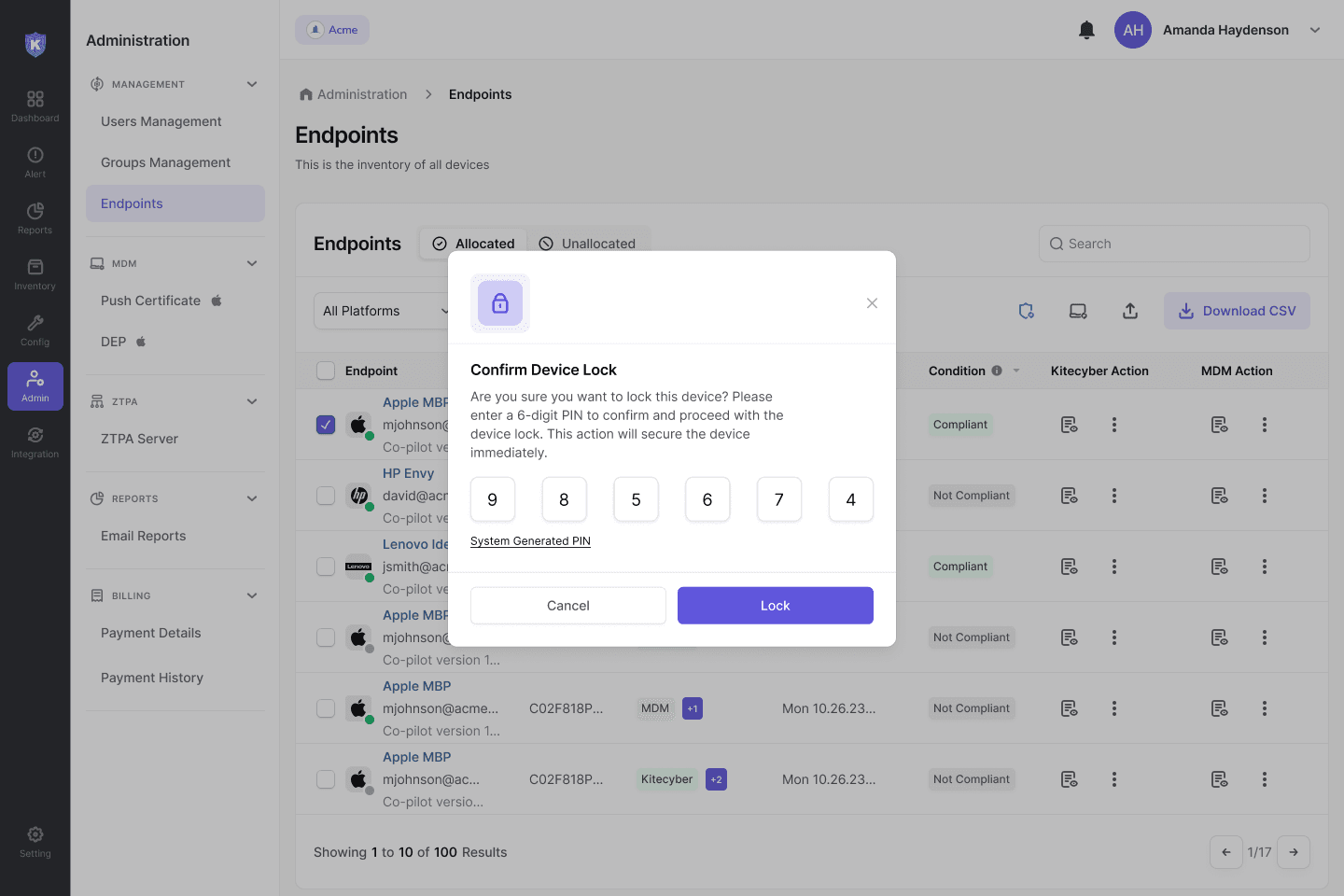
Lock down lost or stolen devices to prevent breaches
Kitecyber’s Remote Lock feature allows administrators to secure endpoints from anywhere, enforcing security policies with a single command. Whether locking out active sessions, enforcing reboots, or applying firmware restrictions, this feature strengthens data security for organizations with remote teams and BYOD policies. Stay in control and mitigate risks—wherever your workforce operates.
Product Benefits
Benefits of our UEM Software
Real-Time Monitoring
Gain visibility into all endpoints & users activity, no matter their location.
Automated Updates
Deploy automated device provisioning, configuration, and management workflows.
Multi-OS Support
Manage Windows, macOS, iOS, Android, and more.
Remote lock & wipe
Lock & wipe sensitive data before it gets stolen or uploaded.
Why Kitecyber?
Secure each endpoint before & after delivery
- Before Kitecyber UEM
- Managing desktops, laptops, and mobile devices is fragmented & difficult.
- Lack of visibility creates compliance gaps and security vulnerabilities.
- BYOD policies increase the risk of unauthorized access and data theft.
- Onboarding and lifecycle management are manual and inefficient.
- After Kitecyber UEM
- Streamline all device management on a unified platform.
- Monitor endpoints in real time to enforce compliance.
- Enable secure BYOD with data encryption and remote lock/wipe.
- Automate provisioning, updates, and decommissioning to reduce errors.
The Kitecyber Advantage
| Device Management & Security | Kitecyber | Other MDM Solutions |
|---|---|---|
Quarantine SaaS Apps and VPN access | Yes | Partial |
Compliance Control/ Automation | Yes | Yes |
Compliance Enforcement | Yes | Partial |
Remote Lock, Wipe, & Device Quarantine | Yes | Yes |
Sensitive data detection on devices | Yes | Yes |
Performance & Scaling | High | Poor scaling & performanceDecryption, re-encryption and traffic hair pinning |
Use-case
Omnipresent endpoint management built for modern businesses
Prevent Data Exfiltration
Monitor and block unauthorized data movements via airdrop usage, copy-paste, content upload, etc.
Meet Compliance Standards
Maintain endpoint compliance with SOC2, HIPAA, GDPR, and more.
Remote workforce device management
Manage every single device, remotely. Control apps, data, and settings effortlessly.
BYOD management
Manage, control, and secure any employee-owned device seamlessly.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Case Studies
Customer Success Stories
Claim your FREE security risk assessment worth $1000 today!
How it works
Frequently asked questions
UEM simplifies IT operations by unifying the management of all endpoints into one central platform. This eliminates the need for multiple management tools for different device types, reduces manual intervention through automation, and improves troubleshooting with real-time insights. As a result, IT teams can deploy policies faster, ensure compliance more easily, and minimize downtime.
A robust UEM solution typically includes:
- Centralized Management: Single dashboard for all device types.
- Lifecycle Management: Device provisioning, updates, and decommissioning.
- Security: Features like remote wipe, encryption, and policy enforcement.
- Automation: Streamlined workflows for software deployment and compliance checks.
- Integration: Compatibility with other IT and security tools like identity management and threat detection systems.
UEM solutions improve security by enforcing consistent policies across all devices, regardless of device type or location. Key security features include:
- Endpoint encryption and data loss prevention (DLP).
- Real-time threat detection and mitigation.
- Remote locking and wiping of lost or stolen devices.
- Granular control over application and network access.
This holistic approach ensures a zero-trust security model is maintained across the organization.
- Healthcare: Securing sensitive patient data on mobile and IoT devices.
- Finance: Ensuring compliance with stringent data protection regulations.
- Manufacturing: Managing IoT devices and securing production environments.
- Retail: Handling point-of-sale systems and employee devices securely.
- Education: Supporting various devices used by students and staff.