Table Of Content
Rise in 3rd party risks and the security challenges, a wakeup call?
-
May 27, 2024
-
Ready to take your security to next level and protect from cyber attacks?
In mid-April 2024, Cisco Duo, a leading provider of multi-factor authentication (MFA) and single sign-on solutions, disclosed a security breach involving one of its third-party telephony providers. This provider is responsible for managing SMS and VoIP services crucial to Duo’s MFA system.
The Incident
What Was Compromised?
- Phone numbers
- Carrier details
- Geographic locations
- Dates and times of messages
- Types of messages

Potential Risks
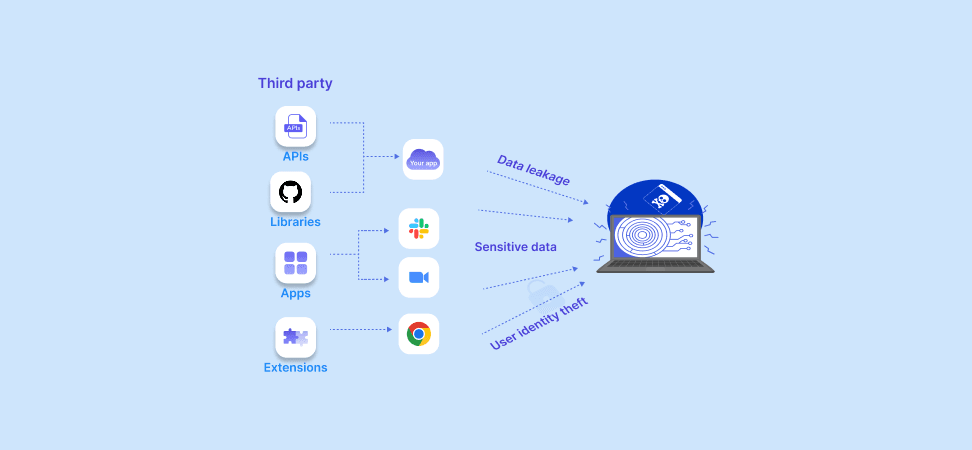
The compromised metadata poses significant risks, primarily due to its potential use in targeted phishing or social engineering attacks. With detailed information about Duo users, attackers could craft highly convincing phishing schemes to deceive users into divulging even more sensitive information.
But Leaked Logs are Harmless, Right?

Response and Mitigation
Conclusion
This breach serves as a stark reminder of the complexities and risks inherent in digital security, further compounded by the interdependence of third and fourth-party providers within the digital infrastructure.
The choices are clear: rely on user education and hope for the best, or implement a robust security layer as part of a comprehensive defense-in-depth strategy. Don’t leave your security to chance. If you’re interested in strengthening your defenses against this ongoing threat, talk to us to learn more about adding this crucial security layer.
Visit our product website to learn more, schedule a demo, or sign up for a free 14-day trial: App Shield