SaaS Security Solution
Discover, Control, & Secure all your sanctioned SaaS, non-SSO SaaS and 3rd party apps
Trusted by Renowned Customers & Partners
Overview
The growing security gaps in SaaS
The Problem
Existing SASE and SSPM solutions fall short in dealing SaaS Sprawl
Access Vulnerabilities
- Access with Magic links and OTPs bypass SSO.
- Add-on installs from App marketplaces in super apps like Slack, Zoom, bypass device controls.
- Browser extensions based app deployment evade IT oversight.
Usage Complications
- Weak or lack of RBAC for Agentic apps and prompts compromises security.
- Attackers exploit SaaS accounts as entry points or to move laterally within an organization.
Data Exposure & Compliance Risks
- Unauthorized or unsanctioned SaaS apps lead to untracked data storage and sharing, increasing exposure to breaches.
- Inadequate oversight of sensitive data can result in non-compliance with regulations like GDPR, HIPAA, or PCI-DSS.
- Sensitive data shared with SaaS, Gen AI, and Agentic apps.
These numbers on SaaS sprawl are too good to be true
60%
of Successful Ransomware Attacks Sourced Through SaaS Applications -
New HYCU report
33%
of organizations that paid the ransom still could not recover the data. - 2024 Ransomware Trends Report
55%
of employees are using AI tools and 84% admit to exposing company data. - Grip Security
Product Overview
Introducing App Shield: Kitecyber’s SaaS Security Solution
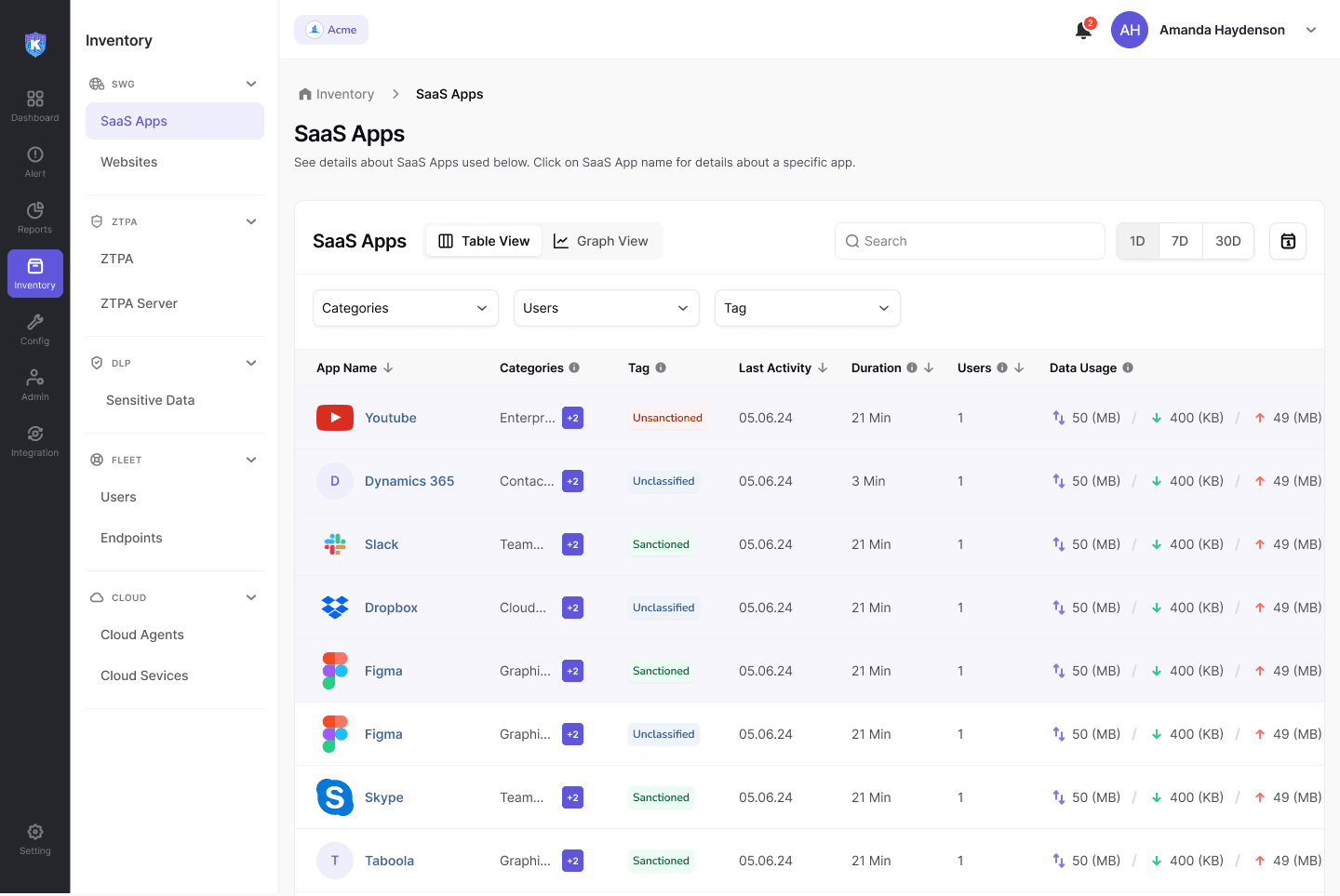
SaaS Discovery & Classification
Sanction, unsanction, and secure your entire SaaS ecosystem
Discover your complete SaaS attack surface in minutes—sanctioned and unsanctioned apps, users, OAuth connections, resources, and more.
Gain full visibility into all SaaS applications, integrations, and inactive or shadow accounts with a trustworthy SaaS inventory. Powered by patented technology, Kitecyber’s agent-based discovery secures both Gen AI and non-AI apps effortlessly.
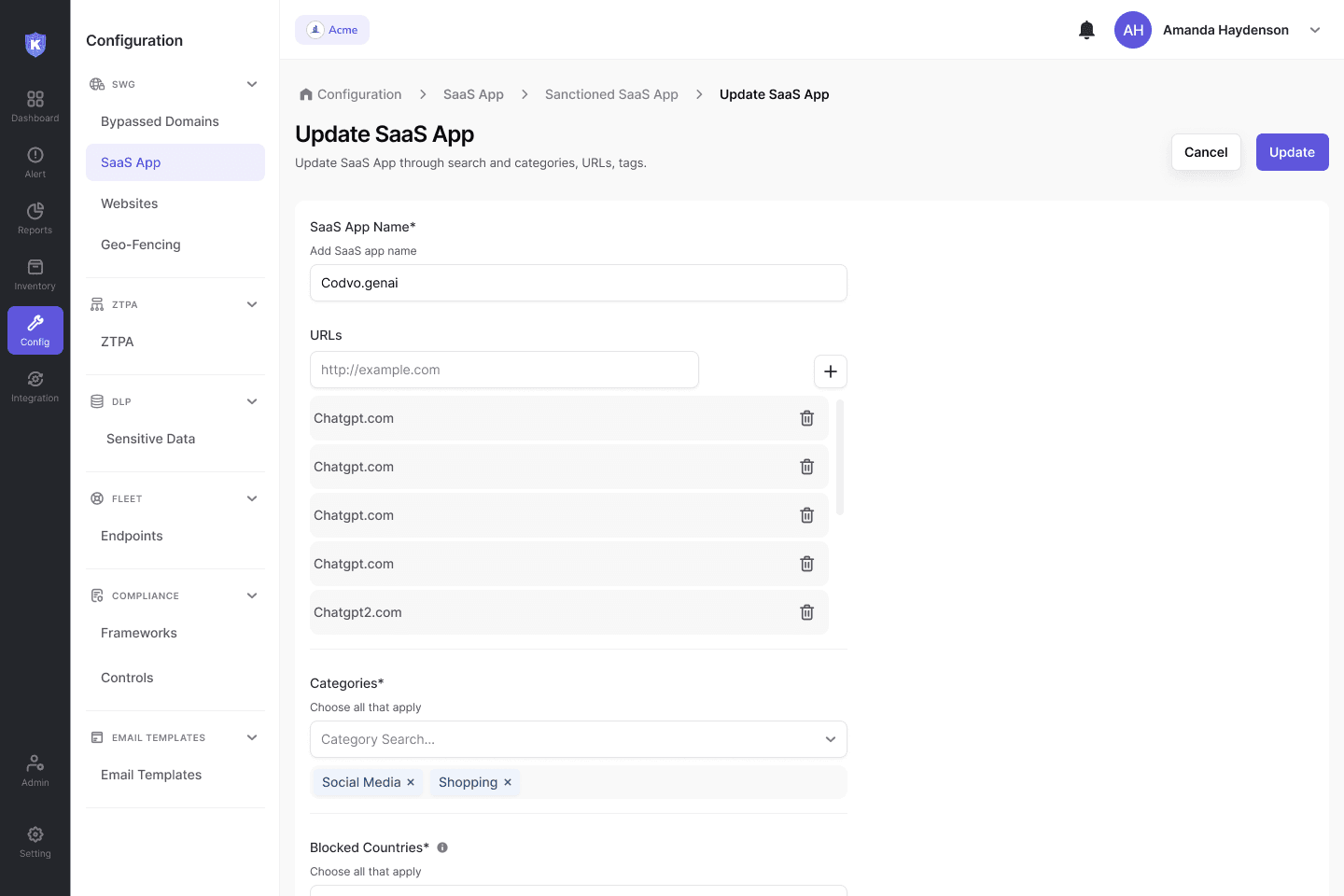
SaaS App Management
Update SaaS apps through categories, URLs, and tags
Kitecyber App Shield lets you update or add new sanctioned SaaS app to be used inside the organization through categorization, URLs, and tagging.
Intelligently block any country access to the SaaS apps and reduce your SaaS attack surface.
Endpoint-based Secure Web Gateway
Control SaaS sprawl at the source with endpoint-based SWG.
Blocking SaaS access frustrates employees and drives risky workarounds. Instead, Kitecyber lets IT security teams classify and secure SaaS apps directly with a Secure Web Gateway (SWG). Kitecyber’s SWG offers custom SaaS-specific controls to limit what users can do within a SaaS application.
Administrators can easily create custom SaaS definitions, specifying which actions to restrict, and then apply them through policy rules—ensuring granular control and enhanced security.
SaaS App Usage
Check screen time of SaaS apps in use
Kitecyber simplifies SaaS management by signifying total screen time consumed by users in a unified view.
With its new SaaS management features, Kitecyber provides IT teams with automated tools to monitor SaaS usage—both sanctioned and unsanctioned. It enables compliance policy enforcements, ensures governance, and offers clear insights into data transfer and memory usage.
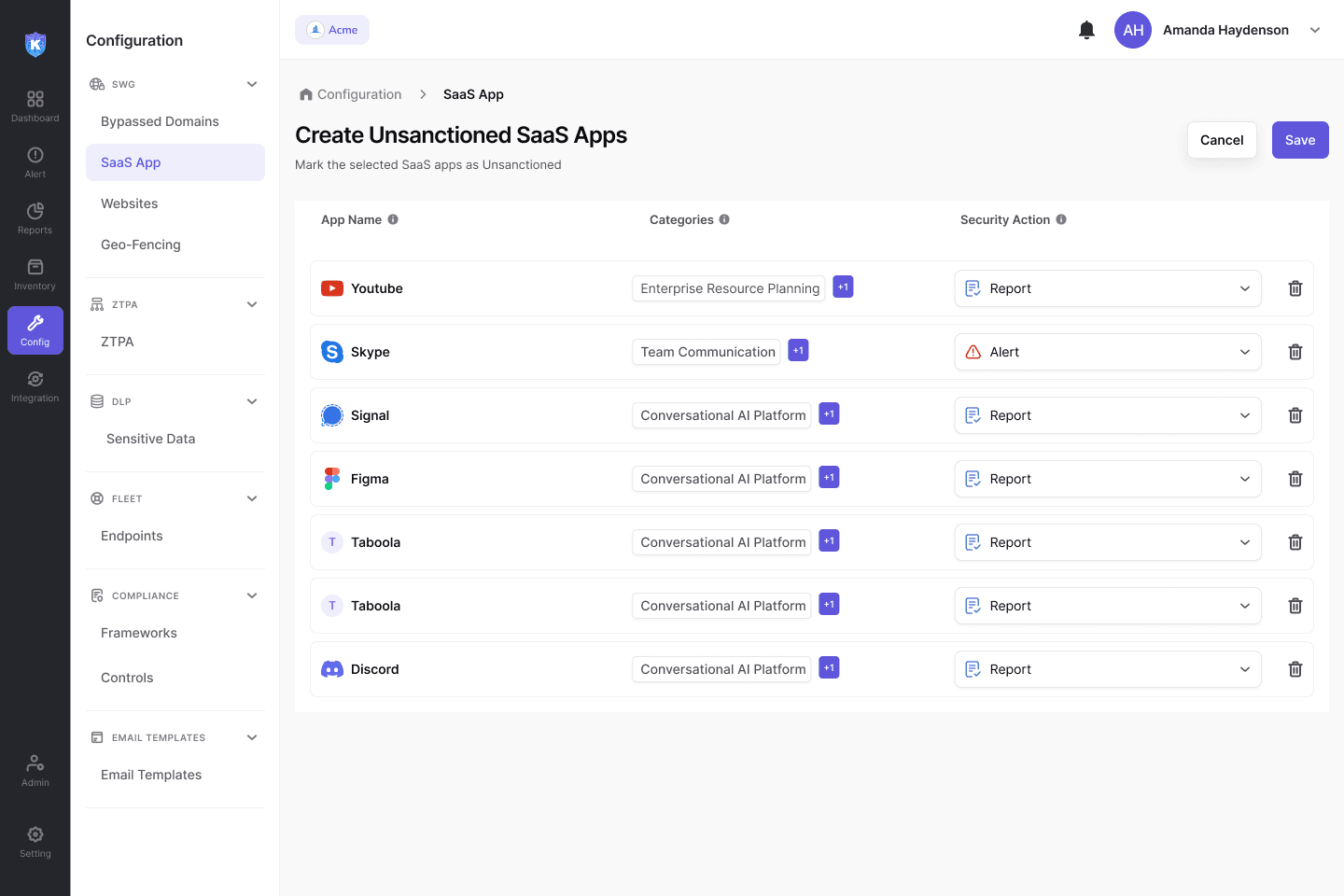
Risk Identification
Identify attack surface risks by creating unsanctioned apps
Reduce your attack surface and enforce granular SaaS security policies with ease.
SaaS Cost Savings
Reduce SaaS Costs by eliminating unnecessary subscriptions
Kitecyber App Shield offers a clear view of potential SaaS app savings. With verified usage insights, it eliminates waste by identifying unused or underused SaaS products and features—no employee surveys needed.
Access actionable data to cancel unnecessary subscriptions, downgrade costly premium plans, and automate SaaS license reclamation based on real-time usage. Achieve continuous governance with ease.
Why choose Kitecyber App Shield?
| SaaS App Access | Kitecyber App Shield | SASE & SSPM |
|---|---|---|
Discovery & Inventory | YesSanctioned, Unsanctioned and previously not seen | PartialSanctioned & Unsanctioned SaaS apps known to SSO or visibility from email providers |
Sensitive data discovery | Yes | PartialYes, if known to SSO, SaaS API and SaaS access logs availability |
Security: SaaS Access & Data Leak | Prevention | DetectionPrevention, if known to SSO or SaaS API availability |
SaaS App configuration posture | No | Yes |
Integrated SaaS, Internet and Private access security | Yes | No |
Audit Trails and Compliance policies | Yes | YesYes, if known to SSO, SaaS API and SaaS access logs availability |
Governance (Onboarding & Off boarding) | Yes | PartialYes, if known to SSO, SaaS API and SaaS access logs availability |
The Kitecyber Difference
- Before Kitecyber App Shield
- Employees use unsanctioned apps without IT's knowledge.
- Magic links and OTPs bypass Single Sign-On (SSO), leaving IT unaware
- The rise of GenAI tools with easy signup options exacerbates shadow SaaS risks
- Apps like Slack and Zoom host native add-ons that evade device management controls
- After Kitecyber App Shield
- IT tracks app usage and user activity in real-time.
- IT authenticate users securely and enforce SSO compliance.
- Detect and manage GenAI tools, ensuring compliance with security policies.
- Monitor and control app integrations and add-ons in native platforms.
Use-case
Kitecyber Secure SaaS Access Use Case
Prevent Link Spoofing
Detect & block links that look legit but aren’t.
Data Security
Monitor and safeguard sensitive information.
Hybrid Work Security
Deliver a secure and seamless work experience, anywhere.
SaaS Sprawl Prevention
Discover and block unsanctioned SaaS apps.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Case Studies
Customer Success Stories
Claim your FREE security risk assessment worth $1000 today!
How it works
Frequently asked questions
Secure SaaS Access refers to the processes, technologies, and policies that ensure secure and seamless access to Software-as-a-Service (SaaS) applications. It involves protecting user identities, enforcing access controls, and monitoring activity to prevent unauthorized access and data breaches, while maintaining optimal user experience.
A Secure Web Gateway (SWG) is a security solution that protects users from online threats by monitoring and filtering web traffic. It enforces policies to block malicious websites, prevent data leaks, and ensure compliance. While effective for traditional web traffic, SWGs often struggle with modern SaaS-specific challenges, such as visibility and app-specific controls.
SaaS Security Posture Management (SSPM) is a solution designed to monitor and secure SaaS applications by identifying misconfigurations, vulnerabilities, and compliance issues. However, it often fails to control SaaS sprawl because:
Decentralized Adoption: Employees adopt SaaS tools without IT approval.
Dynamic Ecosystem: Rapid onboarding of new apps makes it hard to track all tools.
Limited Coverage: SSPM tools focus on configuration management rather than discovering shadow SaaS.
SWGs can introduce errors and outages due to:
Latency Issues: Processing web traffic through a gateway adds delay.
Complex Policies: Misconfigurations in traffic policies can block legitimate traffic.
Incompatibility: Some SaaS apps may not function correctly when routed through an SWG.
These issues can disrupt business operations and frustrate users.
SWGs require extensive setup and maintenance, including:
Policy Management: Creating and maintaining comprehensive policies.
Scalability: Supporting large user bases and high web traffic.
Specialized Expertise: Demanding skilled personnel for proper operation.
High Costs: Licensing fees, hardware, and ongoing management costs.
These factors make SWGs both resource-intensive and costly.
An endpoint-based approach secures SaaS apps directly on user devices, offering:
Granular Controls: Enforcing security policies based on user behavior and context.
Reduced Complexity: Eliminating the need for traffic rerouting through gateways.
Improved User Experience: Ensuring seamless access without introducing latency.
Scalability: Adapting easily to the organization's growth and device diversity.
DNS-based solutions provide basic domain-level filtering but fall short in:
Granularity: Lacking app-specific controls and visibility.
Dynamic Nature of SaaS: Struggling to keep up with rapidly changing app behaviors and subdomains.
Limited Threat Detection: Focusing only on DNS requests and missing broader attack vectors.
For comprehensive SaaS security, more advanced solutions with deep app-level visibility and controls are required.
The key risks of SaaS sprawl usage include:
Data Leakage: Unauthorized sharing or exposure of sensitive information.
Shadow IT: Use of unapproved SaaS apps outside IT oversight.
Access Mismanagement: Improper user permissions leading to breaches.
Compliance Issues: Difficulty in maintaining regulatory standards with SaaS sprawl.